What is CCTV?
“Closed-Circuit Television”, or CCTV, is a system that allows you to keep an eye on what’s happening in and around your business. Monitors and cameras allow you to view what’s happening live, and recorders save footage that can be accessed at a later date for reference. Be sure not to think of business CCTV security monitors as regular television monitors. Publicly broadcasted content is not received on CCTV, only footage from security cameras installed in the facility.

What Services Are Offered With a Business CCTV Security Installation?
Before allowing someone else to control the safety of your building, it’s imperative that you understand what is about to be done and what you should expect from them. The installer that you choose should display that they will go the extra mile and provide you with a service that perfectly fits your needs. Security camera installation is unique with every case and two projects are never the same. The best way to achieve the best installation is to have an open dialogue with your installer.
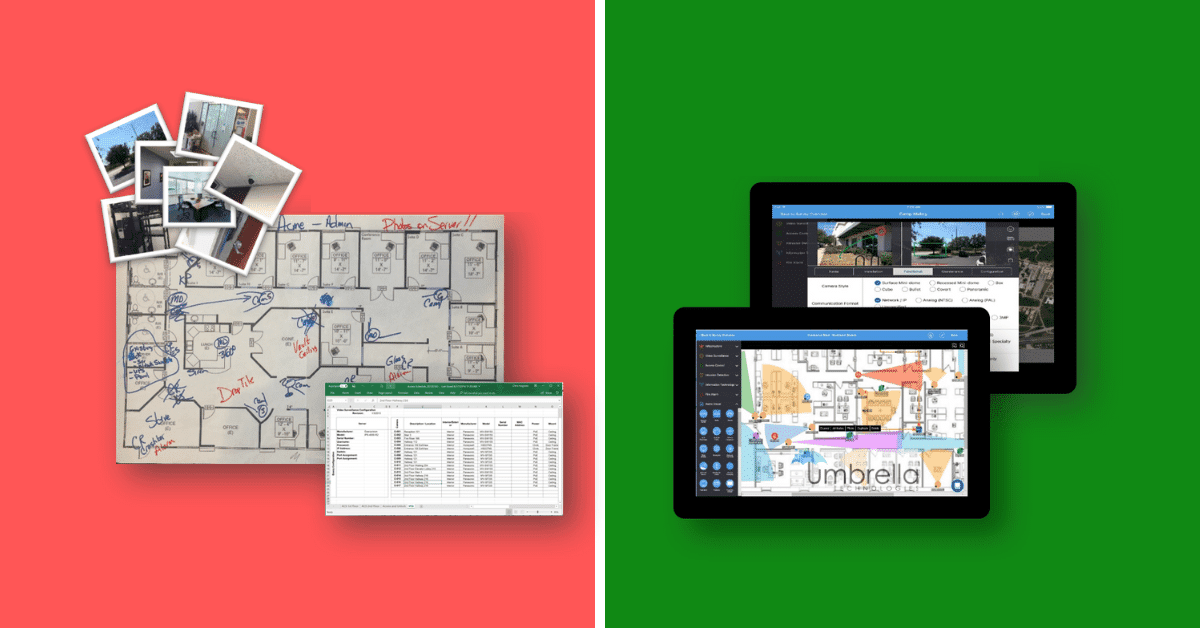
After this, the existing security camera system will be audited. Beginning with an on-site walkthrough or ‘site survey’ would involve analyzing IP or analog based surveillance cameras, cable paths and lengths for low-voltage installation measurements, gaps in coverage, and IDF locations and IT network infrastructure. It’s crucial to give the security system integrator a floor plan that is accurate in order for them to update designs and make notes. A good security system integrator will use a digital design tool during your walkthrough to create a system that prepares for camera installation.
An all-in-one digital CCTV design software will be used to incorporate every aspect of the security system from access control to cable-runs, measurements, images and a visual field-of-view of the proposed surveillance design. After this, a Non-Disclosure Agreement should be done. This protects the end-user as well as allows for facilities confidential information to be shared. Then, a progress agreement is put in place to cover several things such as laying out expectations of the process and its results, identifying insurance coverage, and outlining abilities. Certifications and requirements for insurance are then outlined.
Then, a Pre-Install Check-List Meeting occurs. The system integration company identifies different aspects regarding the installation as well as what technology will work best. Before describing how the system will be installed, preparation will be brought up. In order for the installation to run smoothly, a plan will be put in place from the beginning.

How Exactly Does CCTV Work?
CCTV has been around since the early days of James Bond. However, CCTV has come a very long way since then. So how does a business CCTV system work in the year 2021? It really depends on what type of system is involved. The systems are characterized by the types of cameras that are used: Typically IP-based cameras.
IP-based cameras work by using an IP (Internet Protocol) network, which is often the same network that the rest of a company uses. If the bandwidth is a problem, a different network using category 5 wiring can be used. Either way, video info is recorded to a server, which means that video information can be located either on-site or remotely.
Wired Security Cameras
Wired security cameras use cables to be able to, of course, conduct video surveillance and also transmit footage, however, the signal can weaken when the transmission range exceeds 300 meters. By using the proper networking cables, signal boosters and switches this problem can be solved. Multiple cameras can be interconnected to a single monitor located within a security room.
Analog Cameras
Analog cameras have existed for years. They are still the most commonly used type of CCTV camera installed across the world today. They store video onsite and have basic functionality. Analog is NOT the most commonly used. In fact, it’s rarely used. The overwhelming majority of NEW installations are IP (Network Based) Video Surveillance cameras. Typically, when we see Analog camera installations they are anywhere from 8-15 years old and are overdue for an upgrade. In these situations, it’s always best to design 1st with open-platform video surveillance cameras and software- In some cases we would recommend a Hybrid system which could incorporate the best of both worlds maintaining existing analog cameras while supporting ‘new’ IP based cameras. Alternatively, you can use an encoder to convert the ‘old’ analog cameras into IP.
Internet Protocol Cameras
Internet protocol (IP) cameras have the same functions as analog cameras, however, they have vastly greater capabilities. Internet protocol cameras have higher resolution, sharper images and more flexible features like repositioning and remote zoom. You are also given the option to see your footage on a web browser. This allows you to receive notifications with anything suspicious in your camera records like movement in your business at 2 AM, and you have the capability to view it live anywhere via smartphone or computer. The only drawback to IP cameras is that they cost much more.
Structured Cabling Services
Every business CCTV security system requires an amount of cabling, even ones with wireless cameras. Different cables link contrasting pieces of equipment together including recorders, monitors, wired cameras and modems.
Different situations might require different frame rates for video surveillance.
- 5 frames per second: This might be sufficient for certain scenarios, like monitoring a construction site where you only need occasional updates. It looks noticeably different from real-time video when observed closely.
- 10 frames per second: This frame rate can make video appear closer to real-time, and it’s suitable for many applications. For comparison, Netflix operates at 26 fps, slightly below the standard real-time rate of 30 fps.
- 30 frames per second:This is considered real-time video and is often used in situations where a higher level of detail and smoothness is crucial, especially in environments with potential sudden movements or fast-paced activities.
The choice of frame rate depends on the specific application. For example, a remote construction site might not need 30 fps if you’re just checking progress a couple of times a week. However, in a commercial security setting where there could be unexpected movements, a higher frame rate, like 10 to 15 fps or even 30 fps, might be necessary for accurate monitoring.
Video Recorders
If a CCTV camera spots something, a recorder within the system ensures that you can go into the previous footage and watch it later. Cameras can be set up to record everything that is captured, however, that takes up a lot of storage space. You might want to have cameras programmed to record only during specific times or only when movement is detected. There are two options when it comes to video recording. They are DVR and NVR.
-
- DVRs: “Digital Video Recorders” are the modern replacement for analog recorders that used videotapes. DVRs capture footage from analog cameras in digital format at your desired resolution and frames per second. Once the hard disk becomes full, new images will record on top of the oldest footage first.
- NVRs: “Network Video Recorders” work very similarly to DVRs, however, they are compatible with IP cameras. Cameras and NVR connect through a router or network switch. Easy access to footage on an NVR is available through a web browser or mobile app.
Be sure to select surveillance-grade hard disks when choosing DVR or NVR. They are built with more durable segments than regular computer hard drives so they are able to run 24/7 if that is necessary.
Display Unit
In order to view recorded or live footage from your installed security cameras, you have to hook up your DVR or NVR to a monitor or TV. The display unit for your business CCTV security system can range anywhere from an HD color monitor to a simple monochrome screen. If IP cameras are installed, you are also able to view footage remotely from a computer, tablet or smartphone.

Internet Protocol Cameras
Internet protocol (IP) cameras have the same functions as analog cameras, however, they have vastly greater capabilities. Internet protocol cameras have higher resolution, sharper images and more flexible features like repositioning and remote zoom. You are also given the option to see your footage on a web browser. This allows you to receive notifications with anything suspicious in your camera records like movement in your business at 2 AM, and you have the capability to view it live anywhere via smartphone or computer. The only drawback to IP cameras is that they cost much more.
Structured Cabling Services
Every business CCTV security system requires an amount of cabling, even ones with wireless cameras. Different cables link contrasting pieces of equipment together including recorders, monitors, wired cameras and modems.

What is Physical Security?
Physical security stands for the protection of the data, people, and property at your business from damage or harm. All must be secured, from customers and employees to networks and computers, to all of the equipment within your property.
Why is Physical Security Important to Businesses?
In this crazy age we live in with phishing, hacking and social engineering, it can be very easy to forget about environmental or physical security. However, physical security is emphatically as important as its cybersecurity counterpart. Physical security threats can be external or internal, acts of nature or manmade. Businesses should rely on logical physical and cybersecurity programs to protect the physical assets of an organization, whether it be hardware or people. Network firewalls, IDS/IPS systems or DMZ are all worthless if a criminal is able to walk right into your facility and steal a drive. All organizations should lessen tangible threats in their areas which include service or utility interruptions, sabotage, natural disasters or malicious insiders.
How to Mitigate Physical Security Threats
Certain physical threats are more easily mitigated than others are. It would be much easier to bar entry to a malicious insider by using access control practices. Those could include badge swipe door locks, for example. Like logical security, no amount of money can stop threats entirely, however it is the responsibility of the organization to execute its due diligence to curtail the impact of the loss of business cohesion. There are many ways to mitigate risk in physical space, such as:
- Access Control
- Site Layout
- Utility Redundancy
- Intrusion Protection and Detection
- Elemental Protection
Business and Organizational Layout
Your business’s site layout is very important in protecting it’s contained assets. Hardware and even people can fall victim to crime, eavesdropping/voyeurism, weather, and emergencies if not prepared. Designing a low-profile layout can help to prevent all of those potential threats. For example, lower visibility could be the difference between a criminal breaking into your facility or the one next door to it. The fewer access points your facility has, like external doorways, the better. It’s important to consider using an access control keycard system. Store equipment containing sensitive information in areas without windows and analyzed access.
Access Control
Access control within your business is absolutely essential. It prevents strangers, visitors, and vendors from obtaining access to information or equipment that they otherwise should not have access to. RFID (Radio Frequency Identification) cards alone could ensure that the public is deterred away from having access to sensitive information, equipment or assets. These methods will, in turn, provide an audit trail, which can be very valuable because an insider’s movements inside the building will be tracked.
Intrusion, Protection, and Detection
In using secondary security equipment such as closed-circuit cameras and motion detectors complements the use of keycards If the key process were corrupted, the system would be alerted to a trespasser via motion detection and the entirety of the event would be recorded.
Utility Redundancy
Your business is also a target and can face threats from large outside forces that might seem non-threatening, such as participating in the local power grid. Any person operating on a local power grid is susceptible to a breach if the power goes out because of overuse. A backup plan for your utilities lessens the impact of a threat by keeping your network disturbance-free. Businesses that rely on the uptime of their equipment should include power redundancy within their security program so they can remain in operation while the utility company works to restore service.
Elemental Protection
Fascinatingly, natural disasters are a very real threat to physical security, specifically in areas where landslides, tornadoes, flooding, and earthquakes are common. It’s important to be prepared:
- When choosing to open a new office and relocate, understand the environmental threats specific to that area
- Incorporate preventative measures if you are aware that a storm is coming
- Plan your space appropriately so it has the proper safeguards
- Monitor local weather reports
As an example, if your business is in Tornado Alley, your physical security plan should include construction with thick concrete walls in some or all of the facilities. It should also include at least a single room with no windows. This gives peace of mind that employees and all in the building will be safe in case of a storm.
Implementing Physical Security
A risk analysis is the best place to start identifying the vulnerabilities of your physical space and its impact. The analysis is able to evaluate crime reports, historical weather, natural phenomenon, and man-made hazards, which will help your administration prioritize each threat. By defining threats, you’ll be able to determine what your minimum physical security needs will be. If your facility is in a coastal area that is prone to flooding and hurricanes, for example, mitigation against these elements takes priority over mitigating against earthquakes and requires a different strategy to handle. Next, up, baseline countermeasures should be developed. These items will be the minimum physical security features you obtain to avoid any lost assets. This includes features such as:
- Earthquake-proof server racks
- Elevated floors
How Can CCTV Surveillance Improve Overall Business Security?
CCTV surveillance systems have made much progress in the last ten years not only in the ability to interact with other security technology but also in individual capability. Many industry experts say that CCTV can be used in three primary ways: for forensic purposes, as an interdictive device or as a deterrent. CCTV originally began as a deterrent. There was the notion that “Big Brother” was always watching was just enough to keep people from acting poorly. However, today, CCTV systems are so common that they have lost their uniqueness, which reduces its effectiveness as a deterrent.
As video analytics have become more efficient, CCTV systems have evolved into a forensic tool, gathering evidence after something has happened. However, as CCTV has become more easily integrated with alarm systems, monitoring devices, and access control devices, a third use of CCTV is gathering momentum: assisting security personnel to interrupt and identify security breaches as they are happening or even before they happen. The most advanced video algorithm is facial recognition, but most experts agree that this technology is as efficient now as it will be many years later
In conclusion, implementing CCTV into your business’s security system will not only benefit you now but also far down the line, making it a fantastic investment to any business owner.

